Security Applications for Embedded Vision
Vision security, or intelligent video, provides perimeter intrusion detection
Vision products have been used in the physical security market for a number of years. The technology is commonly referred to as video content analysis (VCA) or intelligent video in the physical security industry. It is used in virtual tripwire applications, providing perimeter intrusion detection for high-risk facilities such as airports and critical infrastructure.
Typical projects use video analytics to generate real-time alerts when an object is identified and tracked through a pre-defined area. Operators, based in the central control room, can manage more video streams as they are not required to identify intruders purely from watching the monitors. Instead, the vision product will identify and alert the operator when there is a potential security issue. It is then up to the human operator to decide how best to deal with the threat.
Other applications of vision products in the security space include wrong-way detection and trajectory tracking. These types of algorithm can be used in airport exit lanes, where security managers want to identify people entering the restricted area from the main terminal. This responsibility has historically been given to security guards; however, vision technology can reduce security guard costs for airport operators and increase the accuracy of the security system.
Other applications in the security market include behavior recognition algorithms such as “slip and fall” and abandoned/left object detection. These applications are less developed than the perimeter detection systems, but will provide powerful tools for security managers over the coming years.
What are the primary vision products used in security?
The primary vision products in the physical security market are network cameras, encoders, NVRs (network video recorders), DVRs (digital video recorders) and intelligent appliances. Established video surveillance vendors supply the majority of these products. These vendors either develop analytics in-house or embed third party algorithms from video content analysis software developers. Consequently, growth in the market is heavily driven by what these vendors decide to do and the extent to which they commit to intelligent video.
Over the last couple of years, the video surveillance market has also seen “low-end” analytics, such as camera tamper detection and video motion detection, become a standard feature on many vendors’ product ranges. These applications have developed from a distinct video analytics market to a product feature used as a differentiator. “Low-end” analytics are embedded on cameras, encoders and storage devices.

D3 Embedded Showcases Camera/Radar Fusion, ADAS Cameras, Driver Monitoring, and LWIR solutions at CES
Las Vegas, NV, January 7, 2026 — D3 Embedded is showcasing a suite of technology solutions in partnership with fellow Edge AI and Vision Alliance Members HTEC, STMicroelectronics and Texas Instruments at CES 2026. Solutions include driver and in-cabin monitoring, ADAS, surveillance, targeting and human tracking – and will be viewable at different locations within

Qualcomm’s IE‑IoT Expansion Is Complete: Edge AI Unleashed for Developers, Enterprises & OEMs
Key Takeaways: Expanded set of processors, software, services, and developer tools including offerings and technologies from the five acquisitions of Augentix, Arduino, Edge Impulse, Focus.AI, and Foundries.io, positions the Company to help meet edge computing and AI needs for customers across virtually all verticals. Completed acquisition of Augentix, a leader in mass-market image processors, extends Qualcomm Technologies’ ability to provide system-on-chips tailored for intelligent IP cameras and vision systems. New Qualcomm Dragonwing™ Q‑7790 and Q‑8750 processors power security-focused on‑device AI across drones, smart cameras

The End of Point-to-Point Security: Why AI Agents Exceed the Single Pane of Glass
This blog post was originally published at Camio’s website. It is reprinted here with the permission of Camio. AI is transforming security from a cost center into decision infrastructure. 1. Why the Old Security Model Reached Its Limits How the Single Pane of Glass Hit a Ceiling For decades, the security industry chased an elusive “single

ST Introduces New Image Sensors for Industrial Automation, Security and Retail Applications
Four new 5MP image sensors allow customers to optimize image capture with high speed, high detail with a single, flexible product instead of two chips New device family is ideal for high-speed automated manufacturing processes and object tracking New sensors leverage market-leading technology for both global and rolling shutter modes, with a compact 2.25µm pixel

“Deep Sentinel: Lessons Learned Building, Operating and Scaling an Edge AI Computer Vision Company,” a Presentation from Deep Sentinel
David Selinger, CEO of Deep Sentinel, presents the “Deep Sentinel: Lessons Learned Building, Operating and Scaling an Edge AI Computer Vision Company” tutorial at the May 2025 Embedded Vision Summit. Deep Sentinel’s edge AI security cameras stop some 45,000 crimes per year. Unlike most security camera systems, they don’t just… “Deep Sentinel: Lessons Learned Building,

How AI-powered Cameras Are Transforming Data Center Security
This blog post was originally published at e-con Systems’ website. It is reprinted here with the permission of e-con Systems. Data centers process, store, and transmit enormous volumes of data. So, it makes them natural targets for intrusion, sabotage, and other violations. Learn about the importance of AI-based camera surveillance in data centers and their

Capgemini Leverages Qualcomm Dragonwing Portfolio to Enhance Railway Monitoring with Edge AI
This blog post was originally published at Qualcomm’s website. It is reprinted here with the permission of Qualcomm. AI device powered by Qualcomm Dragonwing boosts productivity and reduces cloud dependence in Capgemini’s monitoring application for grade crossings Capgemini moved from their previous hardware solution to an edge AI device powered by the Qualcomm® Dragonwing™ QCS6490

The Role of Embedded Cameras in Ensuring Perimeter Security
This blog post was originally published at e-con Systems’ website. It is reprinted here with the permission of e-con Systems. Any breach along the perimeter, from industrial plants to data centers, results in major threats. That’s why embedded vision is so important. Discover how cameras work in these systems, their must-have features, as well as
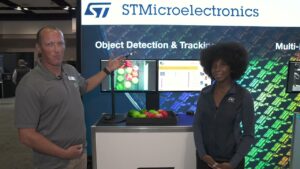
STMicroelectronics Demonstration of Real-time Object Detection and Tracking
Therese Mbock, Product Marketing Engineer at STMicroelectronics, and Sylvain Bernard, Founder and Solutions Architect at Siana Systems, demonstration the companies’ latest edge AI and vision technologies and products at the 2025 Embedded Vision Summit. Specifically, Mbock and Bernard demonstrate using STMicroelectronics’ VD66GY and STM32N6 for real-time object tracking, ideal for surveillance and automation.

Network Optix Demonstration of How the Company is Powering Scalable Data-driven Video Infrastructure
Tagir Gadelshin, Director of Product at Network Optix, demonstrates the company’s latest edge AI and vision technologies and products at the 2025 Embedded Vision Summit. Specifically, Gadelshin demonstrates how the company’s latest release, Gen 6 Enterprise, is enabling cloud-powered, event-driven video infrastructure for enterprise organizations at scale. Built on Nx EVOS, Gen 6 Enterprise supports
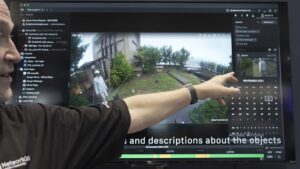
Network Optix Demonstration of Seamless AI Model Integration with Nx AI Manager
Robert van Emdem, Senior Director of Data Science at Network Optix, demonstrates the company’s latest edge AI and vision technologies and products at the 2025 Embedded Vision Summit. Specifically, Van Emdem demonstrates how Nx AI Manager enables seamless deployment of AI models across a wide variety of hardware, including GPU, VPU, and CPU environments. van
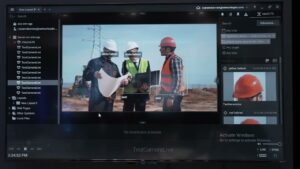
Network Optix Demonstration of Extracting AI Model Data with AI Manager
Marcel Wouters, Senior Backend Engineer at Network Optix, the company’s latest edge AI and vision technologies and products at the 2025 Embedded Vision Summit. Specifically, Wouters demonstrates how Nx AI Manager simplifies the extraction and use of data from AI models. Wouters showcases a live model detecting helmets and vests on a construction site and

Network Optix Overview of the Company’s Technologies, Products and Capabilities
Bradley Milligan, North America Sales Coordinator at Network Optix, demonstrates the company’s latest edge AI and vision technologies and products at the 2025 Embedded Vision Summit. Specifically, Milligan shares how Network Optix is enabling scalable, intelligent video solutions for organizations and industries around the world, including by using Nx EVOS and Nx AI Manager. Learn

“Rapid Development of AI-powered Embedded Vision Solutions—Without a Team of Experts,” a Presentation from Network Optix
Marcel Wouters, Senior Software Engineer at Network Optix, presents the “Rapid Development of AI-powered Embedded Vision Solutions—Without a Team of Experts” tutorial at the May 2025 Embedded Vision Summit. In this presentation, Wouters shows how developers new to AI can quickly and easily create embedded vision solutions that extract valuable information from camera streams. He

Imaging Trends in 2025: Shaping the Future of Security and Surveillance
This blog post was originally published at Visidon’s website. It is reprinted here with the permission of Visidon. A couple of weeks ago, we had the opportunity to exhibit at ISC West 2025 in Las Vegas—the flagship global event for security and surveillance professionals. As always, this show served as a crystal ball for the

AI-generated Heat Maps Keep Seniors and their Privacy Safe
This blog post was originally published at NVIDIA’s website. It is reprinted here with the permission of NVIDIA. By 2030, more than one in five Americans will be 65 or older, becoming the United States’ largest group of seniors ever. Silicon Valley-based startup Butlr has developed an AI platform designed to keep seniors safe while

